We upgraded the agents with updated version of curl to better support testing sites with SSL and ciphers that were only supported via command line options passed into curl.
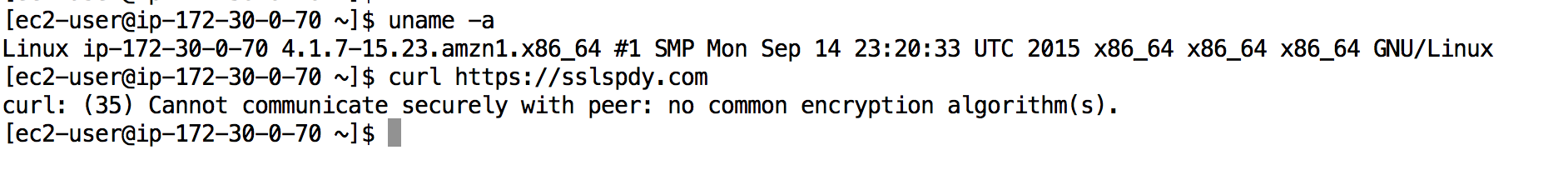
A user reported that testing a site such as https://sslspdy.com would return an error
Cannot communicate securely with peer: no common encryption algorithm(s).
This is noted as a resolved issue in RHEL (curl does not support ECDSA certificates) and unresolved in Fedora (NSS does not enable ECC cipher-suites by default)
and as summarized on this serverfault answer
The common factor with both of these sites is that they use ECC SSL certificates to secure their https connections, rather than the traditional RSA certificates used by most sites. These are currently very rare, but they are expected to increase in popularity in the future.
Both the versions of curl and NSS in use were built with ECC and therefore ought to support these certificates, so I think you’ve run into a bug in Fedora and should report it. A related bug was recently fixed in RHEL 7.
This is visible in a vanilla AWS AMI as well
After updating to recent branch of curl and using –with-sssl this issue is resolved. If you want to confirm on your account you can clone this simple url test – https://www.redline13.com/share/testplan/17947
Rebuilding Curl
For those that have this issue on their own servers or projects, we posted more of the details below. If you want test on your own server and rebuild curl here are the quick steps we used for curl on centos, in my case standard AWS AMI.
#1 Get the parameters used to build your current CURL from the command line
sudo su yum install libcurl-devel curl-config --configure // update options to use --with-ssl
#2 Some packages required
yum install git libtool openssl-devel gnutls-devel nss-devel libssh2-devel
#3 Going to need the source code
git clone https://github.com/bagder/curl.git cd curl
#4 Configure and Build Steps
./buildconf ./configure '--build=x86_64-redhat-linux-gnu' '--host=x86_64-redhat-linux-gnu' '--target=x86_64-amazon-linux-gnu' '--program-prefix=' '--prefix=/usr' '--exec-prefix=/usr' '--bindir=/usr/bin' '--sbindir=/usr/sbin' '--sysconfdir=/etc' '--datadir=/usr/share' '--includedir=/usr/include' '--libdir=/usr/lib64' '--libexecdir=/usr/libexec' '--localstatedir=/var' '--sharedstatedir=/var/lib' '--mandir=/usr/share/man' '--infodir=/usr/share/info' '--disable-static' '--enable-symbol-hiding' '--enable-ipv6' '--enable-ldaps' '--enable-manual' '--enable-threaded-resolver' '--with-ca-bundle=/etc/pki/tls/certs/ca-bundle.crt' '--with-gssapi' '--with-libidn' '--with-libssh2' '--with-ssl' '--with-nss' 'build_alias=x86_64-redhat-linux-gnu' 'host_alias=x86_64-redhat-linux-gnu' 'target_alias=x86_64-amazon-linux-gnu' 'CFLAGS=-O2 -g -pipe -Wall -Wp,-D_FORTIFY_SOURCE=2 -fexceptions -fstack-protector --param=ssp-buffer-size=4 -m64 -mtune=generic' make make install
#5 Test
curl https://sslspdy.com
Success.